You may have already heard in the news about another widespread ransomware attack taking down large companies, hospitals, and transportation systems around Europe and the U.S. Labeled “NotPetya” by security authority Kaspersky Lab, it uses the same Windows vulnerability that the Wannacry ransomware did just a few weeks ago. The Safety Net team, including Senior Security Engineer Jeff Mertz, is aware and watching the latest on this one.
Protection in Place
Here’s the good news: when Microsoft released the patch that closed the “EternalBlue” hole that was allowing that criminal software to get in, Centralized Services Manager Shawn Edie and CS Technician Josh Lichty went to work on a big project ensuring every single computer and server in all of our Your Net clients’ networks had it. They scanned again this afternoon to be sure, and found only one among thousands of client computers that wasn’t already patched (and are working with that client to rectify right away). Remote monitoring and management tools installed on machines allow us to confirm this, and illustrate why it’s so important those tools are in place. As of this writing, no clients have been affected by NotPetya.
Suspect a NotPetya Infection?
Because no system is fail-safe, if a screen appears that looks like the one pictured here, the most important thing to know is to power that computer down and don’t try to power it back up before getting us involved. This is especially important with NotPetya.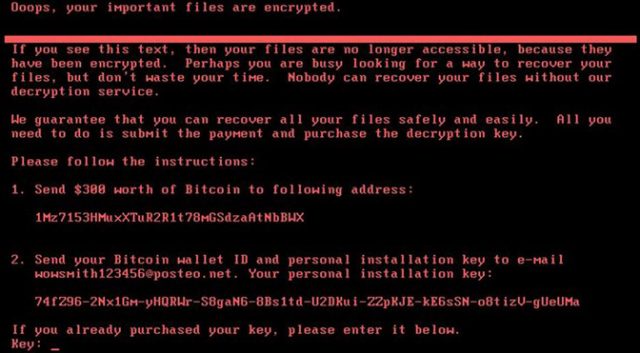
It only takes one computer on your network to make a hole that lets malware in. This is a great opportunity to remind your colleagues to be diligent and use good security practices that protect your organization. Wouldn’t we all rather be enjoying a nice glass of wine tonight than dealing with a nightmare like this?
As always, you can contact our Support Services team with any IT security concerns.


