What is it?
Have you ever received a code on your phone that you had to enter on Google or Amazon to finish logging in? That’s a form of multi-factor authentication. Entering only a username and password is considered single-factor authentication. Multi-factor authentication requires another level of protection, more than just a password, to access an account. Two-factor authentication, referred to as 2FA, is the most familiar form of multi-factor authentication.
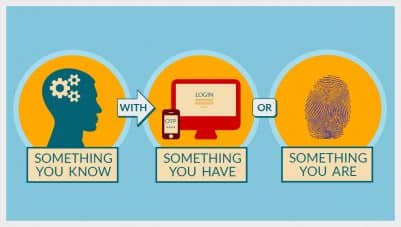
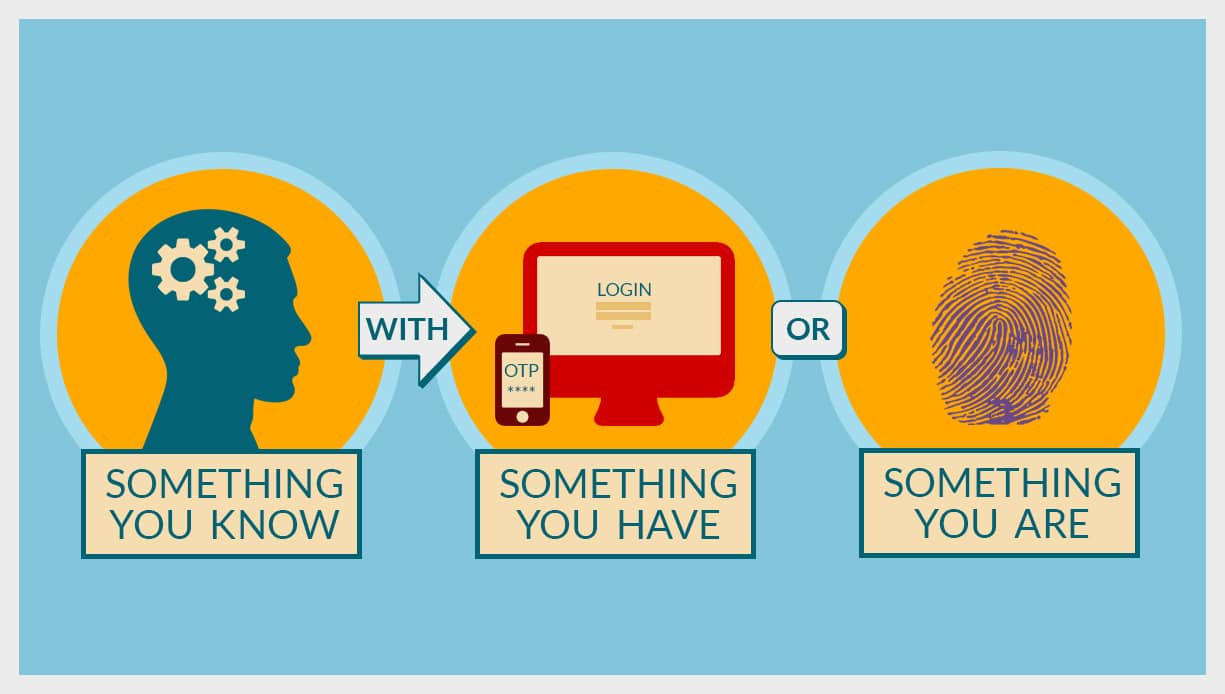
Establishing authentication requires a combination of at least two of three credentials:
• Something you have
• Something you know
• Something you are
Without even realizing it, you use 2FA for simple, everyday tasks. For example, when you stop for gas, you slide your credit card at the pump (factor one – something you have) and enter your zip code (factor two – something you know). To get past the front counter at the gym, you show a membership card (factor one – something you have), tell the attendant your name (factor one – something you know), and/or place your finger on the print reader (factor three – something you are).
Two-Factor for Business
Large companies, governments and the military have used forms of multi-factor authentication since the 1980’s. Fortunately, like many things from the 80’s, technology has come a long way! The services and hardware required for 2FA are becoming widely available and more affordable, making it increasingly attainable for small and midsize businesses.
As businesses face stringent compliance requirements, security continues to be a major concern. Controlling access to specific areas of your building, maintaining confidential files, and locking down access to hardware to prevent unauthorized use are all important steps in developing a security plan. 2FA helps.
Passwords aren’t Enough
A password isn’t always enough when restricting access to a system, whether it be a laptop, a software application, or a physical location. Over the past few years, we’ve all learned passwords are hacked. We strongly recommend the use of a password phrase rather than a password with special characters. That’s likely a change from what you’ve heard in the past. A study by Microsoft revealed that collectively, humans spend the equivalent of over 1,300 years each day typing passwords! Between remembering multiple passwords with varying character requirements, typing unusual combinations, and resetting forgotten passwords, previous password guidelines actually have a negative impact on productivity. Choose a sentence that is easy to remember – “My dog Tucker sits outside, even in the rain!” Create a passphrase from that sentence – “Dog Tucker outside rain!”
Regardless of the rules used for selecting a password, a keylogger can compromise anything typed into a computer (or mobile device). A keylogger is malware that captures the keystrokes entered on a keyboard and communicates them over the internet to a remote server. The computer user usually doesn’t know it’s happening. There are preventive measures for these things, of course, like enforcing strong password policies on your company network and ensuring there are proven IT procedures in place. Conducting checks and performing regular maintenance will help make sure the bad guys aren’t getting in. Two-factor authentication offers another level of protection.

What Two-Factor Looks Like
In the business world, the “something you have” is often a physical device like a Yubikey, pictured here. You carry it on you, and when you need to log in, you plug it in a USB port. When you press the button, it feeds through randomized characters that the system recognizes. To log in, however, you must also enter something you know, like a four-digit PIN. The computer or the key can be stolen, but your brain cannot. The bad guys are often on the other side of the globe, so you’d have to hold some pretty important info for them to get on a plane and track you down! While it’s not impossible for a hacker to break through 2FA, having it in place makes you a more challenging target. Hackers are lazy and don’t like challenges.
There are other 2FA devices that achieve the same goal but get there in a different manner. Those who have worked in banking or in the corporate world anytime since about 1995 would probably recognize the RSA SecureID token. It displays a series of numbers in a little window that looks like a calculator’s output. The algorithm-generated numbers change every 60 seconds or so on RSA’s end. The system accepts only the numbers showing at that moment.
Two-Factor in the Future
The next advances are coming in the form of biometrics – “something you are.” Many smartphones, including iPhones, can capture a read of your fingerprint. The Samsung Galaxy S8 recently introduced iris scanning and facial recognition. The accuracy of biometrics still needs to improve, but that ever-present mobile device is a convenient means of authentication. You might forget to grab your Yubikey, but you rarely leave your house or office without your phone, right?
Which Option Now?
While development of the “something you are” factor continues, 2FA users are, for the most part, stuck carrying a little token. However, using newer 2FA applications with your mobile device can eliminate the need for additional devices. Many two-factor authentication deployments now allow ‘push notifications.’ A PIN is pushed (auto-generated) to your mobile device for you to enter or accept. Or a prompt is pushed and you accept it just by touching the screen. One such offering is available from Michigan-based Duo Security.
When wondering why you need 2FA, remember, two locks are better than one! When deciding which solution to implement, keep in mind, the most effective security solution is one that people will actually use, and people like things that are easy to use!